The post CUSTOMER ALERT – CVE-2022-22963: Remote Code Execution in Spring Cloud Function appeared first on Waratek.
]]>CVE-2022-22963 is a critical-severity vulnerability affecting Spring Cloud Function versions 3.1.6, 3.2.2 and older unsupported versions. When using routing functionality it is possible for a user to provide a specially crafted Spring Expression Language (SpEL) expression as a routing-expression that may result in remote code execution and access to local resources.
Based on what we know now, can Waratek Java products remediate this vulnerability?
Yes. Waratek recommends enabling the ARMR Process Forking rule to prevent remote code execution via data binding and remediate CVE-2022-22963. A custom ARMR Remediation Patch will not be required and customers with the ARMR Process Forking rule already in place are currently secured against CVE-2022-22963.
Does the vulnerability impact any third party tools I use with Waratek solutions?
We strongly recommend that all customers check third party support and advisory sites. If you have any questions or concerns, you can also contact our Customer Support team at support@waratek.com.
Non-Waratek customers should request a trial license or a live demonstration of Waratek’s protective agents.
About Waratek
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
Waratek is the winner of the 2020 Cyber Defense Magazine’s Cutting Edge Award for Application Security, the Cybersecurity Breakthrough Awards 2019 Overall Web Security Solution of the Year, and is a previous winner of the RSA Innovation Sandbox Award along with more than a dozen other awards and recognitions.
The post CUSTOMER ALERT – CVE-2022-22963: Remote Code Execution in Spring Cloud Function appeared first on Waratek.
]]>The post CUSTOMER ALERT – CVE-2022-22965: Spring Framework RCE via Data Binding on JDK 9+ appeared first on Waratek.
]]>CVE-2022-22965 is a critical-severity vulnerability affecting Spring MVC or Spring WebFlux applications running on JDK 9+. When running on Tomcat as a WAR deployment your applications may be vulnerable to remote code execution (RCE) via data binding. If your application is deployed as a Spring Boot executable jar (the default) it is not vulnerable to the exploit.
Based on what we know now, can Waratek Java products remediate this vulnerability?
Yes. Waratek recommends enabling the ARMR Process Forking rule as well as the ARMR File-System Write rule to prevent file writes to the Apache Tomcat folder.
Waratek is also providing all customers an ARMR Remediation Patch that’s functionally equivalent to a vendor patch and will alleviate the need for the ARMR File-System rule.
Contact your Waratek Customer Success Managers for assistance in applying the instant ARMR Remediation Patch at customersuccess@waratek.com.
Does the vulnerability impact any third party tools I use with Waratek solutions?
We strongly recommend that all customers check third party support and advisory sites. If you have any questions or concerns, you can also contact our Customer Support team at support@waratek.com.
Non-Waratek customers should request a trial license or a live demonstration of Waratek’s protective agents.
About Waratek
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
Waratek is the winner of the 2020 Cyber Defense Magazine’s Cutting Edge Award for Application Security, the Cybersecurity Breakthrough Awards 2019 Overall Web Security Solution of the Year, and is a previous winner of the RSA Innovation Sandbox Award along with more than a dozen other awards and recognitions.
The post CUSTOMER ALERT – CVE-2022-22965: Spring Framework RCE via Data Binding on JDK 9+ appeared first on Waratek.
]]>The post Java Vulnerability CVE-2013-5838 patched in 2013 re-emerges appeared first on Waratek.
]]>Rated by Oracle in 2013 as 9.3 out of 10 on the Common Vulnerability Scoring System (CVSS), CVE-2013-5838 [Common Vulnerabilities and Exposures (CVE) database] can be exploited remotely, without authentication, to completely compromise a system’s confidentiality, integrity and availability.
Waratek’s innovative Runtime Application Security Protection (RASP) solutions protect data and applications from vulnerabilities in current and legacy Java versions without patching. We protect the full application stack using a pioneering virtual container technology that operates in the runtime.
Using Waratek’s RASP containers with a default security policy, CVE-2013-5838 is automatically mitigated and no specific security rule for this CVE is required. Default security policies work in one of two ways: either reducing the severity of a given vulnerability, or eliminating the vulnerability altogether. In the case of CVE-2013-5838, a default security policy immediately reduces the severity of this vulnerability to partial and eliminates the complete compromise of the host computer system and its data. This benefit is achieved with no foreknowledge of this CVE or the nature of its exploit.
Learn how Waratek can improve your application security with an easy to install, cost efficient, highly effective solution that does not degrade application or network performance and produces zero false positives*.
*Yes, we know that sounds too good to be true, but we can prove it! Just ask for a technical demonstration and we’ll show you how easily and quickly you can improve your application security with Waratek.
The post Java Vulnerability CVE-2013-5838 patched in 2013 re-emerges appeared first on Waratek.
]]>The post Waratek Names Douglas Ennis Chief Executive Officer appeared first on Waratek.
]]>With over 20 years’ experience ranging from application development, internal IT, consulting and sales, Doug has a proven track record and deep understanding of the cybersecurity and networking landscapes. Prior to joining Waratek as Chief Revenue Officer in May of 2021, Doug has held sales leadership roles in companies focused on data privacy, network security, application performance management and mobile device management. In his elevated role, Doug will focus on driving deeper penetration of Waratek’s award-winning technology into the expanding cybersecurity verticals and sectors.
“Between Doug’s background in the security industry and his track record for achieving strong business growth and development, he’s the right person to take Waratek to the next level,” said Chris Rouland, Board Director at Waratek. “With application security threats intensifying across many industries, Waratek is positioned for rapid growth over the next few years and Doug’s stewardship will play an important role in making that happen.”
Ennis adds, “Waratek has built a culture of relentless innovation and agility that allows us to help customers meet today’s evolving threat landscape. Today, I am thrilled to lead Waratek into its next phase, as we expand our patented Autonomous Rule Management Runtime platform (ARMR) to provide API security, and move towards becoming the first fully programmable Application Security Platform to defend both your applications and APIs.”
“Everything we do at Waratek is built around our culture and Doug’s infectious energy has inspired the team from day one,” said John Matthew Holt, Founder of Waratek. “His grasp of the underlying capabilities of our patented security innovations within the ARMR Platform and the possibilities of future challenges we can solve for, makes me very excited to see where Doug leads us in the years ahead.”
To learn more about how Waratek delivers runtime security and real-time protection, visit https://www.waratek.com/.
About Waratek:
Leading global companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
Contact
Jacob Warren
312-964-8541
The post Waratek Names Douglas Ennis Chief Executive Officer appeared first on Waratek.
]]>The post Latest Oracle Critical Patch Update Addresses 497 Vulnerabilities, Highest Number Ever appeared first on Waratek.
]]>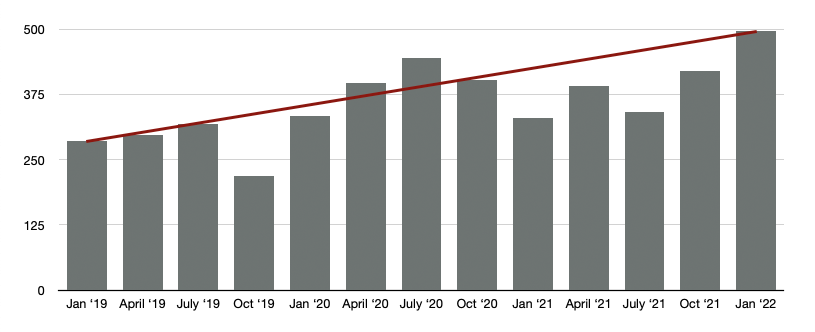
The increase of CVEs suggests that there are 5.5 new CVEs per day. If you go to bed having patched your application to 100%, by the time you wake up, get to the office, and have your morning coffee, you’re already 2 CVEs behind. In the current security climate when you’re not actively taking a step forward, you’re taking a step back.
Given the upward trend of vulnerabilities and the increase in severity, what can you do to protect yourself?
The Paradox of Progress
The best way to address the vulnerabilities to apply the Critical Patch Update as soon as possible. However as I explained above, due to the sheer volume and rate at which new vulnerabilities come out, that may not even be enough.

The moment the CPU is released, hackers begin reverse engineering the binaries as seen in the example above from October 2020. Once they have bypassed the fixes, they often receive rewarding feedback such as:

Look, my intent here is not to criticize the efficacy of, nor the effort that goes into the CPU. Applying the patches is an important action, but there’s only two sure fire ways to increase your security posture and truly prevent exploits:
- Dedicate sufficient human capital to fix the vulnerable code
- Leverage a security platform that autonomously fixes the vulnerable code in memory
Both of these options are valid solutions, however, only one of them has a predictable investment. Hiring a team of people to constantly review and test code in real-time, patch the new CVE that comes out every several hours, just isn’t feasible.The effort and cost alone would be uncontrollable and unscalable. Leveraging an autonomous solution is not only scalable, but the investment is affordable and predictable.
Decreasing Your Security Risk Profile
You may be thinking to yourself, “Yeah, I get it, I can only solve this if I spend money on another security solution. Shocker.” You may even already use a typical solution that scans code for vulnerabilities that it’s aware of. However, being aware of the vulnerabilities is only one-half of the way towards a solution.
WAFs may seem like a logical step for securing your applications, but it’s important to remember that they’re not a failsafe solution. WAFs are fraught with problems like:
- Generation of false positive and false negatives
- Lack protection against Zero-Day exploits
Perhaps the most important limitation is the fact that they can be easily bypassed. And when I say “easy,” I mean that by the next day after Log4j was in the news, Twitter was already crawling with bypasses, as seen below.

If WAFs are a step in the right direction, how are we supposed to reliably and scalably strengthen our security posture? To answer that, I present you with an analogy.
If you are allergic to nuts and you are eating at a restaurant, you’re going to scan the menu for any items that contain nuts. You are going to ask the waiter and you’re going to look at your meal when it comes out to see if you can see any nuts in the dish. That’s how the typical solutions work, by scanning, looking for the nuts that they know should not be there.
Now imagine a solution that sits in the kitchen and autonomously removes the nuts from the dish as the chef puts them in. That’s the power of autonomous security at the application runtime.
If that’s how you’re looking to confidently decrease your Security Risk Profile without dedicating internal resources to divert focus to handling the never-ending technical debt, there’s one place to look: Waratek ARMR,
Only Waratek provides a fully programmable security platform, ARMR, that can autonomously remediate vulnerabilities inside the binary code. Unlike other security products that just attempt to block known exploit payloads, Waratek actually remediates the vulnerable code inside an application’s executing code in real-time and with no interruption to service or degradation of performance.
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
For more information on how Waratek can help your organization, contact us.
The post Latest Oracle Critical Patch Update Addresses 497 Vulnerabilities, Highest Number Ever appeared first on Waratek.
]]>The post CUSTOMER ALERT – CVE-2021-45105: Denial of Service in String Interpretation appeared first on Waratek.
]]>CVE-2021-45105 explains how Log4j versions 2.0-alpha1 through 2.16.0 (excluding 2.12.3) allows attackers to cause denial of service when a crafted string is interpreted causing a recursive lookup. As of time when this advisory was posted, Log4j 2.17.0 and 2.12.3 fix this issue by only allowing lookup strings in configuration to expand recursively. Only with Waratek can you keep your dependencies the same and secure your applications without any code changes, preventing errors from occurring due to the removal of the offending class.
Based on what we know now, can Waratek Java products mitigate this vulnerability?
Yes. Only Waratek provides a fully programmable security platform, ARMR, that can remediate vulnerabilities, including CVE-2021-45105. Unlike other security products that just attempt to block known exploit payloads, Waratek actually remediates the vulnerable code inside an application’s live executing code in real-time and with no interruption to service or degradation of performance.
Waratek is providing all customers an ARMR Remediation Patch which permanently remediates this vulnerability for live, executing Log4j code inside any workload or dependency.
Waratek recommends all customers to add the ARMR Remediation Patch for CVE-2021-45105 to their default ARMR security policy for all applications to permanently remediate the vulnerable code that enables this vulnerability. Modern Java applications that aren’t directly reliant on vulnerable versions of Log4j, but that have dependencies that are, will still benefit from the ARMR Remediation Patch.
As with all ARMR Rules and Remediation Patches, this permanent remediation can be applied live to any workload and does not require service restart or downtime to achieve permanent remediation.
Current Waratek customers can download the instant ARMR Remediation Patch via the Download Portal to permanently remediate this vulnerability for all workloads and applications. For assistance in deploying the patch, please contact our Customer Support team at support@waratek.com.
Does the vulnerability impact any third party tools I use with Waratek solutions?
According to Google, “More than 35,000 Java packages, amounting to over 8% of the Maven Central repository (the most significant Java package repository), have been impacted by the recently disclosed log4j vulnerabilities.”
We strongly recommend that all customers check third party support and advisory sites. If you have any questions or concerns, you can also contact our Customer Support team at support@waratek.com.
Non-Waratek customers should request a trial license or a live demonstration of Waratek’s protective agents.
About Waratek
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
Waratek is the winner of the 2020 Cyber Defense Magazine’s Cutting Edge Award for Application Security, the Cybersecurity Breakthrough Awards 2019 Overall Web Security Solution of the Year, and is a previous winner of the RSA Innovation Sandbox Award along with more than a dozen other awards and recognitions.
The post CUSTOMER ALERT – CVE-2021-45105: Denial of Service in String Interpretation appeared first on Waratek.
]]>The post CUSTOMER ALERT – CVE-2021-4104: Remote Code Execution from JNDI Requests appeared first on Waratek.
]]>CVE-2021-4104 explains how Log4j version 1.2 is vulnerable to deserialization of untrusted data when the attacker causes JMSAppender to perform JNDI requests that result in remote code execution. As of time when this advisory was posted, Apache is still processing this vulnerability and recommends ensuring no JMSAppender is configured for now.
Based on what we know now, can Waratek Java products mitigate this vulnerability?
Yes. Only Waratek provides a fully programmable security platform, ARMR, that can remediate vulnerabilities, including CVE-2021-4104. Unlike other security products that just block known exploit payloads. Waratek actually remediates the vulnerable code inside an application’s live executing code in real-time and with no interruption to service.
Waratek is providing all customers an ARMR Remediation Patch which permanently remediates this vulnerability for live, executing Log4j code inside any workload or software version.
Waratek recommends all customers to add the ARMR Remediation Patch for CVE-2021-4104 to their default ARMR security policy for all applications to permanently remediate the vulnerable code that enables their vulnerability. Modern Java applications that aren’t directly reliant on vulnerable versions of Log4j, but that have dependencies that are, will still benefit from the ARMR Remediation Patch.
As with all ARMR Rules and Remediation Patches, this permanent remediation can be applied live to any workload and does not require service restart or downtime to achieve permanent remediation.
Waratek Customer Success Managers are contacting all customers to assist in applying the instant ARMR Remediation Patch to permanently remediate this vulnerability for all workloads and applications. For assistance in deploying the patch, please contact Customer Success at customersuccess@waratek.com.
Does this vulnerability impact any third party tools I use with Waratek solutions?
We strongly recommend that all customers check third party support and advisory sites. If you have any questions or concerns, you can also contact our Customer Support team at support@waratek.com.
Non-Waratek customers should request a trial license or a live demonstration of Waratek’s protective agents.
About Waratek
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
Waratek is the winner of the 2020 Cyber Defense Magazine’s Cutting Edge Award for Application Security, the Cybersecurity Breakthrough Awards 2019 Overall Web Security Solution of the Year, and is a previous winner of the RSA Innovation Sandbox Award along with more than a dozen other awards and recognitions.
The post CUSTOMER ALERT – CVE-2021-4104: Remote Code Execution from JNDI Requests appeared first on Waratek.
]]>The post CUSTOMER ALERT – CVE-2021-45046: Remote Code Execution from JNDI Requests appeared first on Waratek.
]]>CVE-2021-45046 has been upgraded from a “LOW” CVSS Score of 3.7 to a “CRITICAL” 9.0 and explains how Log4j version 2.15.0 allows attackers to leak information using JNDI Lookup pattern and execute remote code in some environments. As of time when this advisory was posted, Log4j 2.16.0 and 2.12.2 fix this issue by removing support for message lookup patterns and disabling JNDI functionality by default. Only with Waratek can you keep your dependencies the same and secure your applications without any code changes, preventing errors from occurring due to the removal of the offending class.
Based on what we know now, can Waratek Java products mitigate this vulnerability?
Yes. Only Waratek provides a fully programmable security platform, ARMR, that can remediate vulnerabilities, including CVE-2021-45046. Unlike other security products that just attempt to block known exploit payloads, Waratek actually remediates the vulnerable code inside an application’s live executing code in real-time and with no interruption to service or degradation of performance.
Waratek is providing all customers an ARMR Remediation Patch which permanently remediates this vulnerability for live, executing Log4j code inside any workload or dependency.
Waratek recommends all customers to add the ARMR Remediation Patch for
CVE-2021-45046 to their default ARMR security policy for all applications to permanently remediate the vulnerable code that enables this vulnerability. Modern Java applications that aren’t directly reliant on vulnerable versions of Log4j, but that have dependencies that are, will still benefit from the ARMR Remediation Patch.
As with all ARMR Rules and Remediation Patches, this permanent remediation can be applied live to any workload and does not require service restart or downtime to achieve permanent remediation.
Current Waratek customers can download the instant ARMR Remediation Patch via the Download Portal to permanently remediate this vulnerability for all workloads and applications. For assistance in deploying the patch, please contact our Customer Support team at support@waratek.com.
Does the vulnerability impact any third party tools I use with Waratek solutions?
According to Google, “More than 35,000 Java packages, amounting to over 8% of the Maven Central repository (the most significant Java package repository), have been impacted by the recently disclosed log4j vulnerabilities.”
We strongly recommend that all customers check third party support and advisory sites. If you have any questions or concerns, you can also contact our Customer Support team at support@waratek.com.
Non-Waratek customers should request a trial license or a live demonstration of Waratek’s protective agents.
About Waratek
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
Waratek is the winner of the 2020 Cyber Defense Magazine’s Cutting Edge Award for Application Security, the Cybersecurity Breakthrough Awards 2019 Overall Web Security Solution of the Year, and is a previous winner of the RSA Innovation Sandbox Award along with more than a dozen other awards and recognitions.
The post CUSTOMER ALERT – CVE-2021-45046: Remote Code Execution from JNDI Requests appeared first on Waratek.
]]>The post CUSTOMER ALERT – Information on CVE-2021-44228: Remote Code Injection on Log4j appeared first on Waratek.
]]>Posted in the GitHub Advisory Database, CVE-2021-44228 explains how Log4j versions prior to 2.15.0 are subject to a remote code execution vulnerability via the ldap JNDI parser. As of time when this advisory was posted, GitHub is still processing the vulnerability and advises to check back later for any additional information.
Based on what we know now, can Waratek Java products mitigate this vulnerability?
Only Waratek provides a fully programmable security platform, ARMR, that can remediate vulnerabilities, including CVE-2021-44228. Unlike other platforms that just block vulnerabilities, Waratek actually remediates vulnerabilities inside an application’s live executing code in real-time and with no interruption to service.
Customers who have applied ARMR’s Socket:Connect rules to restrict connections to external locations have immediate mitigation for this vulnerability. Additionally, Waratek is providing all customers an ARMR Virtual Remediation Patch which permanently remediates this vulnerability for live, executing Log4j code inside any workload or software version.
Waratek recommends all customers to add the ARMR Virtual Remediation Patch for CVE-2021-44228 to their default ARMR security policy for all applications to permanently remediate the vulnerable code that enables this vulnerability. As with all ARMR Rules and Virtual Patches, this permanent remediation can be applied live to any workload and does not require service restart or downtime to achieve permanent remediation.
Waratek Customer Success Managers are contacting all customers to assist in applying the instant ARMR Remediation Patch to permanently remediate this vulnerability for all workloads and applications. For assistance in deploying the patch, please contact Customer Success at customersuccess@waratek.com.
Does the vulnerability impact any third-party tools I use with Waratek solutions?
We strongly recommend that all customers check third party support and advisory sites such as Elasticsearch and others, as the GitHub Advisory is still processing. If you have any questions or concerns, you can also contact our Customer Support team at support@waratek.com.
Non-Waratek customers should request a trial license or a live demonstration of Waratek’s protective agents.
About Waratek
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
Waratek is the winner of the 2020 Cyber Defense Magazine’s Cutting Edge Award for Application Security, the Cybersecurity Breakthrough Award’s 2019 Overall Web Security Solution of the Year, and is a previous winner of the RSA Innovation Sandbox Award along with more than a dozen other awards and recognitions.
The post CUSTOMER ALERT – Information on CVE-2021-44228: Remote Code Injection on Log4j appeared first on Waratek.
]]>The post Customer Alert – 10/19/2021 appeared first on Waratek.
]]>
Comments from Waratek Founder John Matthew Holt
On Java 17 Security: It’s clear that attention is being paid to security in Java 17. There is the continued work on the hardening. Encapsulating the JDK internals and the removal of remote method invocation activation mechanism. All these things would have been unheard of years ago, but now Oracle and the community are driving these through and the reason they’re doing them is for security.
I think the thing that people need to bear in mind, not only with Java 17 but the future versions of Java, is that as the JDK is going to be making changes to try to improve the security posture of their application, it is going to break their application. It is going to affect their application whether from a performance perspective or from a compatibility perspective.
On the State of Application Security: Patching is not working, is the way I would summarize it. It hasn’t worked for a long time. It’s not about to start spontaneously working now.
Just as we’re seeing the evolution of automobiles from manual driving and as we look five years and 10 years into the future, you know, with the rise of these self-driving vehicles you can set your destination and then sit back and put your hands on your head and relax while the car takes you there. The same is happening in security, and we’re seeing the same kind of rise of, if I can extend that metaphor, full self-driving security agents that attach to your app. You set the destination where you want to go. I want no insecure deserialization. I want no process forking, no SQL injection, and the agent will drive itself there and achieve that outcome for you without you having to do anything for it.
Listen to John Matthew’s full commentary on Java 17 Security and on the State of Application Security.
Other highlights include:
- There are 18 patches for the Oracle E-Business Suite; 4 of the CVEs can be remotely executed. The highest CVSS score is 8.1.
- There are 38 patches for Oracle Fusion Middleware; 30 of the CVEs can be remotely executed. Three (3) have a CVSS score of 9.8.
- There are 17 patches for Oracle PeopleSoft; 8 of the CVEs can be remotely executed. The highest CVSS score is 9.1.
- There are 15 Java SE patches that address CVEs, 13 of which can be remotely executed. Nine (9) of the patches fix flaws as far back as Java SE 7u311. There are 8 patches for the recently released Java 17.
- There are no indications any of the CVEs pathed in the October 2021 Critical Patch Update are currently being exploited in the wild.
Next Steps
Non-Waratek customers should follow the recommended guidelines from Oracle for manually propagating the updated binary patches to your development and test environments, before moving into production.
For Waratek customers, a far simpler process applies. Waratek Patch and Waratek Upgrade customers will receive ARMR virtual patches that address the Oracle CPU CVEs as part of their agreements. Waratek Secure customers will receive ARMR policy recommendations for enabling built-in CWE mitigations that activate zero-day protection with zero tuning or configuration.
In all cases Waratek customers achieve immediate protection to their production applications with no downtime or interruption of service. With Waratek’s range of security agents, customers are protected in five minutes or less.
About Waratek
Waratek is the winner of the 2020 Cyber Defense Magazine’s Cutting Edge Award for Application Security, the Cybersecurity Breakthrough Award’s 2019 Overall Web Security Solution of the Year, and is a previous winner of the RSA Innovation Sandbox Award along with more than a dozen other awards and recognitions. For more information,
visit www.waratek.com.
The post Customer Alert – 10/19/2021 appeared first on Waratek.
]]>